Travis is wondering how he can update his Windows PC to he is not vulnerable to the Meltdown bug.

Travis is wondering how he can update his Windows PC to he is not vulnerable to the Meltdown bug.
Jason Howell and Megan Morrone talk to Ed Bott from the Ed Bott Report on ZDNet about what every Windows Admin needs to know about Spectre and Meltdown and four steps to keeping a level head during this vulnerability and the next. Plus, what might have happened if the update had been able to come out on Microsoft’s Patch Tuesday as planned, instead of being rushed because of the embargo breach.
Curt Franklin, Brian Chee, and Lou Maresca discuss the recent vulnerabilities in Dell’s EMC and VMware units. EMC Avamar, EMC NetWorker, EMC Integrated Data Protection Appliance, and vSphere Data Protection all carry risks that can give attackers root access.
Leo Laporte and Roberto Baldwin try out the new Multi-Room Music feature on the Amazon Echo. We’ll set up several Echos in the studio to set it up and find out how it works. Anker has a new sister brand for smart-home devices called Eufy. One of their latest products is a tiny smart speaker called the Genie. We’ll see how to compares to the Echo Dot. Megan Morrone continues her #DigitalCleanse. This week is number four: Cleaning up your cloud storage. We’re going to revive an old Mac Pro (mid-2010) for our ‘Call for Help,’ and install NVIDIA’s flagship gaming GPU the GeForce GTX 1080 Ti. We’ll take a first look at Tovala’s meal kit service that cooks itself in a smart oven that can steam, bake, and broil. Jason Howell shows us some AR apps on the Asus Zenfone AR. In the ‘Mail Bag,’ we answer questions about what to do with vintage computers and tracking apps for Android.
– Apple to unveil the next iPhone September 12th at the new Apple campus.
– Juicero shuts down and won’t sell juice packs.
– In an email snafu, Essential shared driver’s licenses numbers of some customers.
– Roberto was at the Hyperloop Pod Competition where the winning pod hit over 200MPH.
By Michael Kan | PCWorld
A new Trojan that can steal your payment data will also try to stymie you from alerting your bank.
Security vendor Symantec has noticed a “call-barring” function within newer versions of the Android.Fakebank.B malware family. By including this function, a hacker can delay the user from canceling any payment cards that have been compromised, the company said in a blog post.
Fakebank was originally detected in 2013. It pretends to be an Android app, when in reality, it will try to steal the user’s money.
The malware works by first scanning the phone for specific banking apps. When it finds them, the Trojan will prompt the user to delete them and install malicious versions of those same apps.
The newer variants of Fakebank.B, however, will do more than just collect financial login data. They will also monitor whatever phone calls are made.
If the customer service numbers of certain banks are dialed, the Trojan will cancel the call, Symantec said. Instead, users will have to use email or another phone to reach their banks.
So far, this new Trojan has only been detected in Russia and South Korea. Symantec is advising users refrain from downloading apps from less trustworthy sources, like third-party app stores.
The call-barring function shows how banking Trojans are continuing to evolve. Earlier this year, Symantec detected another kind called Android.Bankosy that can bypass voice-based two-factor authentication systems.
To do this, the Trojan will secretly activate call forwarding on the victim’s phone. All calls will then be redirected to the hacker’s own number.
By Shawn Knight | TechSpot
One of the many ways that cybercriminals earn income is through affiliate advertising programs like Google’s AdSense. Rather than generate traffic through content creation, hackers figure out ways to trick advertising platforms into thinking a partner is sending them legitimate traffic. Not knowing they’re being scammed, the advertising platform pays the partner for the referral.
Such is the case with a clickbot known as Redirector.Paco which Bitdefender Labs detailed on Monday.
According to the security firm, Redirector.Paco has been active in the wild since September 2014. On an infected system, whenever you perform a query on a popular search engine like Bing, Google or Yahoo, the search results are replaced with affiliate links which, when clicked, generate revenue for the hacker.
Bitdefender Labs says the malware is able to redirect traffic by making a few simple registry tweaks on the infected system which tells the browser to send the traffic to a different address. The malware attempts to make the search results look authentic although there are signs – like messages in the status bar referencing a proxy – that indicate something is amiss.
Lengthy load times are also an indicator of infection, Bitdefender Labs said.
The malware has infected more than 900,000 IPs worldwide, most of which are located in Algeria, Brazil, Greece, India, Italy, Malaysia, Pakistan and the US. The payload is typically injected into modified installers for trusted programs including Connectify, WinRAR, KMSPico, Start8, Stardock and YouTube Downloader.
By Justin Luna | Neowin
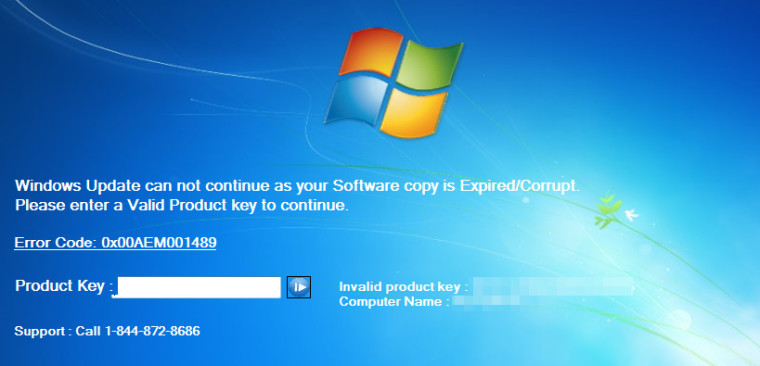
Some of us may be very well aware of the classic tech support scam stories, where a man randomly calls people, and informs them that they are from “Windows company” and that the call recipient’s computer has been detected full of viruses. These cold callers then use fake Blue Screen of Deaths, and make the victim think there really is something wrong with their PC.
Tactics like these can be easily terminated, with the use of a few built-in Windows tools, as well as a few keystrokes. However, scammers have been seen improving their game, and are now incorporating lock screens, in order to threaten a user even more.
This technique can be attributed to the infamous ransomware, where a malicious program encrypts a user’s computer files, and sets a PC to be stuck on a lock screen prompting them to pay up.
As for this one, the scammers trick the victims into thinking that their Windows’ license has expired, and then removes any ability for the user to control their computer. “This is not a fake browser pop up that can easily be terminated by killing the application or restarting the PC. No, this is essentially a piece of malware that starts automatically, and typical Alt+F4 or Windows key tricks will not get rid of it,” according to Jérôme Segura of Malwarebytes Labs.
There is an entire ecosystem on how these malware are being distributed, one of which includes bundling them into Pay Per Install applications. “What you thought was a PC optimizer or Flash Player update turns out to be a bunch of useless toolbars and, in some cases, one of these lockers,” said Segura.
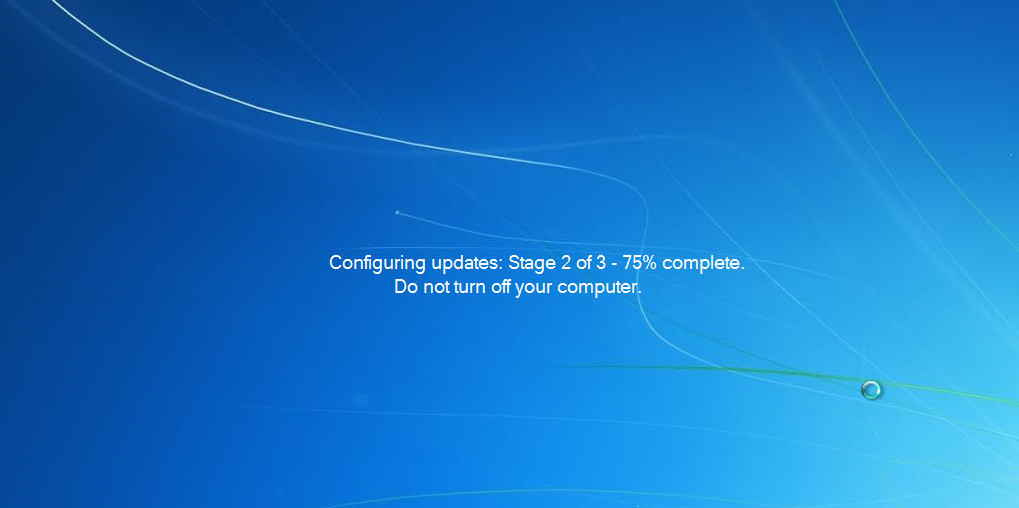
A security researcher, @TheWack0lian has shared a sample on how the new tech support scam tactic works. Through a genuine-looking Microsoft program, which installs without any particular incident, the malware waits for the user to restart their system. Upon rebooting, a user will be welcomed by what looks like Windows configuring updates, though this is already the malware kicking in.
Once its “process” is done, it displays an error screen saying that the user’s Windows license is expired. It even takes the time to display the user’s current license key and computer name, to make it look more legitimate.
Now, to be able to unlock the system, the only choice a user has is to dial the number flashed on the screen, leading them into the said cold tech support scammers who are eager to steal victims’ personal information, as well as their credit card number. Calling the number, it was discovered by the researchers that there is a hidden functionality to the locker. Pressing Ctrl+Shift+T will display an installer for TeamViewer, a remote access computer program. However, the scammer refused to proceed with unlocking the computer unless a payment of $250 is made.
Fortunately, the researchers were able to find a way to bypass the lock screen. Victims of the said issue can press Ctrl+Shift and then the S key. Alternatively, a user can enter either “h7c9-7c67-jb” or “g6r-qrp6-h2” or “yt-mq-6w” into the “Product Key” field to be able to unlock the PC. This however, might only work for some versions of the rogue program.
With these kinds of programs rapidly evolving right before our eyes, it is very alarming to see how much these kinds of malware can take many innocent and susceptible people hostage, and play on their fears in addition to stealing money from them.
It always pays to be wary of where we always go on the internet, as well as what links we click on. Also, a good security software is always handy, to be able to block out the malware that can possibly not only ruin our computers, but also possibly a part of our lives.
By Rob Thubron | TechSpot
You have to be at least 13 years old to have an account on Instagram, but this didn’t stop one 10-year-old Finnish boy from exposing a vulnerability in the Facebook-owned photo-sharing application and winning $10,000 for his work.
Helsinki-based Jani (his parents didn’t reveal his last name) discovered that he could erase any written content on Instagram by altering code on its servers. Facebook told Forbes that he verified this by deleting a comment the company posted on a test account.
The Facebook spokesperson added that the problem came from a private application program interface not properly checking that the person deleting the comment was the same one who posted it.
“I tested whether the comments section of Instagram can handle harmful code. Turns out it can’t. I noticed that I can delete other people’s comments from there,” Jani told Helskini-based newspaper Iltalehti. “I could have deleted anyone’s – like Justin Bieber’s for example.”
Facebook’s bug bounty program rewards people who identify and report security issues. In the five years since it launched, it has paid $4.3 million to more than 800 researchers for over 2400 submissions. Instagram was added to the program in 2014.
Payouts vary based on the level of risk a bug poses. Considering the average reward last year was only $1780, Jani’s $10,000 shows that Facebook regarded it as a fairly high-level threat.
Jani, who learned his skills by watching YouTube instructional videos, is now the youngest person to receive a reward from the program, beating the record set by a 13-year-old back in 2013. He said he plans to buy a football and new bicycle with some of the money.
Google’s attempted invasion of the Windows desktop is now officially over. The Chrome-maker recently announced that the Chrome app launcher will be removed from Windows, Mac, and Linux in July, though it’ll stick around in Chrome OS. Google says it’s dumping the app launcher in the name of streamlining the browser after discovering that most Chrome users “prefer to launch their apps from within Chrome.”
The app launcher was one of three Chrome browser features that appeared to be specifically designed to turn Chrome into a “platform within a platform” on Windows. In addition to the app launcher—which sat in the taskbar and allowed users to fire up Chrome apps just like a normal desktop program, miming Windows Start menu functionality—Google killed Chrome’s notification center in October. That feature was replaced with native web push notifications, a standardized feature that sites can use across all browsers.
Beyond those two features, Google also created a modern UI version of the browser for Windows 8 that essentially put Chrome OS inside Windows. Microsoft’s decision to do away with Windows 8’s ill-advised dual UI for a more traditional desktop in Windows 10 killed Google’s attempt at “Chrome OS for Windows.”
The impact on you at home: If you’re one of the few fans of Chrome’s app launcher, Google may still provide a way for you to launch Chrome apps from the taskbar. Right now, you can create a desktop shortcut for Chrome apps by typing chrome://apps into the Omnibox, right-clicking an app, and then selecting Create shortcuts. The shortcut can then be dragged from the desktop onto the taskbar. We’re confirming with Google that this functionality will remain once the app launcher goes away and will update this story should the company respond.
By Rob Thubron | TechSpot
There are rare occasions when a consumer outcry can cause a company to reverse an unpopular decision it has made, and it seems Amazon is the latest firm to bow to public pressure. Only one day after an update removed local encryption in its Fire range of products, Amazon has decided to restore the feature.
Amazon said it removed the encryption, which it referred to as “enterprise features,” because customers weren’t using it. One of the features in question allowed owners to encrypt their device with a pin which, if entered incorrectly 30 times in a row, deleted all the data stored on it.
Fire OS 5 was originally released in the fall of last year, but the issue came to light earlier this month when Amazon released an over-the-air update for its older Fire devices to upgrade from OS 4.
The e-commerce giant’s move was particularly surprising when you consider that Amazon is one of the big tech companies filing a court brief supporting Apple in its battle with the Department of Justice. The outcome of the San Bernardino shooter iPhone case could have a profound effect on how firms implement encryption in their products, and whether they should include a backdoor to grant authorities access.
As you would expect, Amazon’s decision wasn’t well received, and the company decided that returning the encryption features would be in everyone’s best interests.
“We will return the option for full disk encryption with a Fire OS update coming this spring,” a spokesperson said. Amazon didn’t state what prompted the company to change its mind, but the amount of negative publicity it received, coupled with the attention from the Apple case, doubtlessly played a big part.